



Call For Papers: The Call for Papers is closed!
Call For Sponsors: The Call for Sponsors is closed!
Register for our Open Source Intelligence Capture the Flag competition here: https://goo.gl/forms/341YQHcSgq1Tc5kr1
1st Place
2nd Place
3rd Place
What is BSides?
BSides is an open platform that gives security experts and industry professionals the opportunity to share ideas, insights, and develop longstanding relationships with others in the community. It is a rare opportunity to directly connect and create trusted relationships with key members of the community.
This will be the eighth BSides conference held in St. John’s.
Where is St. John’s?
St. John’s is located along on the East Coast of Canada, on the northeast of the Avalon Peninsula in southeast Newfoundland. It is the most easterly city in North America.
On Twitter


















![]()
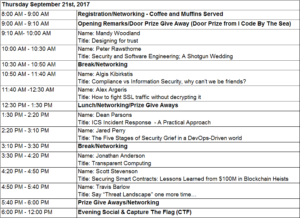
* Please note that Dean Parsons’ talk at 12:45 will NOT be streamed, and as such, will not be available to remote attendees. All other talks will be streamed.

Name: Alex Argeris – Cisco
Bio: Over the last 35 years, Alex has been breaking, fixing and hacking any technology he’s been able to get his hands on. After working many years for large banks and ISPs throughout Canada, he is now working for one of the largest IT vendors in the industry. His modus operandi is to think outside the box.
Title: The Good and the Bad of Cryptocurrency
Abstract: Cryptocurrency has been for a long time associated with criminality and underground community in general. Let’s take a step back to see if it’s still the case. We will look at how you can mine and spend your bitcoins on both side of the legality line. Also you will learn how to play with cryptojacking and how to protect against these new type of attacks.

Name: Dean Parsons – Representing Mr. Boddy of Boddy Manor
Bio: Cybersecurity Leader, Industrial Control System Defender and SANS Instructor for ICS515 – Dean is an active member of the cybersecurity community dedicated to mentoring new comers to the field, and defending Canadian Critical Infrastructure. Dean holds the following security designations – CISSP (Certified Information Systems Security Professional), GSLC (Cybersecurity Leadership), GCIA (Cyber Intrusion Analyst), GRID (Industrial Control System Response and Defense), and a degree in Computer Science from Memorial University of Newfoundland. It’s common to find Dean working at both a packet and policy level, overseeing Security Operations and Active Cyber Defense for an electric utility in Newfoundland. When not focused on security, Dean spends his time exploring the coast of Newfoundland on a JetSki through all seasons, or somewhere on dry land playing piano.
Title: Active Industrial Control System Cyber Defense – Colonel Mustard…Candlestick…Kitchen
Abstract: The presentation draws attention to practical threat detection and incident response from dissecting advanced ICS adversary threat capabilities, tactics techniques and procedures. Dean will illustrate why the Candlestick and the Kitchen are more important than Colonel Mustard for ICS incident response.

Name: Algis Kibirkstis – EthiSecure Services inc.
Title: Fallacy Identifiation for the Information Security Professional or How to Save the Day
Abstract: Organizations no longer have to be convinced that security and privacy are critical business concerns. Yet information security professionals continue to be challenged, at all organizational levels, to justify technological and administrative improvements – challenged by management, engineers, architects, technicians, developers, auditors and even their own peers. We infosec professionals see this coming, so we do our homework, and we always come prepared for genuine and reasonable counterarguments to the strategies and tactics we propose. But how to deal with that individual in the back of the room of a review meeting, that person that has that remarkable ability to completely derail discussions with unsound comments that suck the air right out of the room, leaving everyone else speechless? This tongue-in-cheek presentation will present examples of fallacies used in arguments, describe means of identifying these, and propose ways to steer clear and move forward with your initiatives.

Name: Jared Perry – Patrol
Title: Automating All Security Things With Serverless
Abstract: Is it an oxymoron or your next tool for security automation? Serverless promises to remove the shackles of infrastructure and focus on application code. If you have 1 billion email messages that need processing for malware or maybe need to exfiltrate 10gb of data during a pentest, Serverless could be the answer. Let’s explore what exactly Serverless is and what it can bring to security automation.
Name: Tyler Parrott – Communications Security Establishment
Bio: Tyler Parrott is a Senior IT Security Analyst with the Communications Security Establishment, currently working for the organization’s Cyber Defence program. Tyler has 10 years of experience at CSE, spending 4 years in Vulnerability Research, 3 years with Infrastructure Management & Security, and 3 years on the Malware Analysis & Automation team. Tyler holds a Bachelor’s degree in Computer Science from the University of Ottawa.
Title: CSE’s AssemblyLine and the Canadian Centre for Cyber Security
Abstract: The Communications Security Establishment (CSE), Canada’s national cryptologic agency and a leading expert in cyber security, believes in fostering collaboration and innovation. Learn how those beliefs will be applied to the recently announced Canadian Centre for Cyber Security (CCCS) and gain some insight into its implementation.
Additionally, for the first time ever, CSE has released one of its own tools to the public as an open source platform. Developed internally, AssemblyLine is a cyber defence framework designed to perform distributed analytics at scale, focusing primarily on detecting and analyzing malicious files. Learn how AssemblyLine can not only minimize the number of innocuous files that cyber security professionals are required to inspect every day, but how you can collaborate with others to customize and improve the platform.

Name: Brian Contos
Bio: Brian Contos is the CISO & VP Technology Innovation at Verodin. He is a seasoned executive with over two decades of experience in the security industry, board advisor, entrepreneur and author. After getting his start in security with the Defense Information Systems Agency (DISA) and later Bell Labs, he began the process of building security startups and taking multiple companies through successful IPOs and acquisitions including: Riptech, ArcSight, Imperva, McAfee and Solera Networks. Brian has worked in over 50 countries across six continents. He has authored several security books, his latest with the former Deputy Director of the NSA, spoken at leading security events globally, and frequently appears in the news. He was recently featured in a cyberwar documentary alongside General Michael Hayden (former Director NSA and CIA).
Title: Left of Boom
Abstract: The term “Left of Boom” was made popular in 2007 in reference to the U.S. military combating improvised explosive devices (IEDs) used by insurgents in Afghanistan and Iraq. The U.S. military spent billions of dollars developing technology and tactics to prevent and detect IEDs before detonation, with a goal of disrupting the bomb chain. This is an analog to cybersecurity as we strive to increase the incident prevention capabilities of our security tools and where we can’t prevent attacks, augment prevention with incident detection and response tools.

Name: Hugo Porcher – ESET
Bio: Hugo Porcher graduated from a double degree program in computer security: a M. Eng. from the École de technologie supérieure (Canada) and a B. Eng. from the University of Technology of Troyes (France). He is now working as a Malware Researcher at ESET where he performs analysis of complex threats and tries to conquer the world through the art of reverse engineering. In his free time, he enjoys sliding sports such as surfing and skiing, and expanding his knowledge in reading kryptic technical papers or books and doing CTF challenges.
Title: The Dark Side of ForSSHe
Abstract: In February 2014, ESET researchers from Montreal published a report on a group who compromised more than 40,000 Linux servers worldwide since 2011.
ESET named this campaign Windigo. At the centre of this operation, Ebury, an OpenSSH backdoor which allowed the attackers to remotely take control of compromised servers as well as stealing login credentials (passwords, keys) which were then used to connect to other servers.
This simple yet effective method allowed them to extend their network of compromised servers.
Before the installation of the Ebury backdoor, we discovered that operators collects a handful of information on the newly compromised machine.
Amongst the information gathered, they try to detect the presence of other OpenSSH backdoors potentially installed on the system.
To accomplish this, they wrote a script which search for text or binary patterns in the OpenSSH client and daemon. It includes signatures for more than 40 different backdoors and trigger alerts if the files may be compromised but isn’t covered by a signature. I will show how the script evolved across the years.
As most of those backdoors were unknown to us, we went hunting for them.
In 3 years, we were able to collect hundreds of samples matching the different rules we created base on the signatures. I will present the outcome of the analysis of these samples.
I will take a look at the diverse backdoors we dealt with: both clients and daemons, from off-the-shelves malware to more advanced ones.
From that set of malware samples, we were able to identify patterns and regroup common characteristics across all of them.
Most of the backdoors implemented additional features than just a simple hardcoded password. I will show how they evade logging functionalities of the program, override permissions, etc. Some of them used obfuscation techniques to make analysis harder.
Alongside these capabilities, different methods of data exfiltration were also used.
I will dig into four undocumented families we isolated and identified and talk about the different features they sport.
There will be a variety of techniques discussed as some of these malware went to great lengths to remove their traces from systems, remain under the radar using encryption and custom communication protocol. Infrastructure of some families have been running for years.
To gather more data about the different families we discovered, we have set up a honeypot for their operators to play with. I will detail the custom honeypot infrastructure put in place.
I will show how the attackers operate on a compromised machine and how they deploy their backdoor.
This include the checks they make before deploying their malware, how they install it and the lateral movements we have observed so far.
I will briefly talk about the new backdoor samples we were able to obtain.
Finally, I will sum up what we have learned from this research and give some pointers on preventing this kind of threats. I will see the different prerequisites that operators need in order to install their backdoor and how one can block their attempts.
I will show how to ensure the legitimacy of the OpenSSH daemons and clients and how to detect these backdoors.
Name: Michael Burton
Bio: I am a programmer, game designer, and creative human living in St. John’s. I’m the founder of Perfect Minute Games (http://perfectminutegames.com) and Gamedev NL (http://gamedevnl.org), and I am also the main coordinator for the latter. I graduated Memorial University’s B.Sc. (Joint CS/Physics) degree in 2000 and have been mostly working as a programmer, with a few side trips for creative endeavours.
Title: What Not to Do for Your Game’s Security Systems
Abstract: It is a brief and (hopefully) humorous survey of some of the more visible security issues that have arisen over the last couple of decades in the field of game development. I will discuss the client- versus server-side simulation decisions made by (the original) Duke Nukem 3D and The Division, the spoofing of servers in MMOs such as World of Warcraft, and the evolution of DRM as it applies to both local and networked gaming and its implications for security. I may include other incidents if time allows

Name: Lilly Chalupowski – Go Secure
Bio: Lilly works with GoSecure on Threat Intelligence and started her journey being mostly self-taught making hacking tools in her spare time. Chameleon (custom base64 steganography), Badger (DLL Security Enumeration including ASLR Entropy), Dirty-Needle (DLL Injection Tool) and more. She has presented at the Atlantic Security Conference on PE File Structure Security Enumeration and Custom Base64 Steganography, Hask (Halifax Area Security Klatch) on using file upload vulnerabilities to obtain shell access to a webserver using injection techniques, she has also presented at Digital Discovery Camp for kids on Phishing Awareness and SQLi with interactive demos helping children understand Cyber Security and how to keep an ethical approach, at the same time she is making Cyber Security a more attractive profession to young people.
Title: The Chrome Crusader
Abstract: Crusade into the wild world of malicious browser extensions. You will learn how to do keylogging, cookie stealing, credential harvesting and building a C&C server allowing you to execute arbitrary JavaScript remotely of your choosing. We will also be talking about CORS (Cross-Site Resource Sharing) and some interesting quirks with the browser extension environment. If you are a front-end developer and you want to dive into malicious code this would be the best way to start learning.

Name: Jon Green – Aruba/HPE
Bio: Jon Green is VP and Chief Technologist for Security at Aruba, a Hewlett Packard Enterprise Company. He is responsible for providing technology guidance and leadership for all security solutions including authentication and network access control, UEBA, encryption, firewall, and VPN, and also manages Aruba’s Product Security Incident Response Team (PSIRT) and Aruba Threat Labs, an internal security research group. Jon joined Aruba in 2003 and helped it grow from a small startup to today’s position as a leading provider of network mobility solutions. Jon holds a B.S. in Information Security from Western Governor’s University and a M.S. in Computer Science/Information Security from James Madison University. Jon is part of the Network Operations team at both ShmooCon and DEF CON.
Title: Machine Learning Will Solve All of Our Security Problems
Abstract: Attend any security conference these days and you’ll see an exhibit floor full of information security vendors claiming machine learning (ML) and artificial intelligence (AI). Is this a silver bullet, snake oil, or something in between? We’ll look at different definitions of ML and AI, see how they can solve security problems, and give you tools to cut through the hype.
